In this article, we will show you how to turn on debugging mode while running SSH in Linux. This will enable you to see what actually unfolds when you execute an ssh command to connect to a remote Linux server using the verbose mode or debugging mode.
[ You might also like: 4 Ways to Speed Up SSH Connections in Linux ]
The ssh client’s -v switch allows you to run ssh in verbose mode, which prints debugging information about SSH connection progress, which is really useful for debugging connections, authentication, and any configuration problems.
There are different levels of verbosity; using multiple -v flags increases the verbosity (maximum verbosity level is 3).
ssh -v– will inform you what is happening mostly on your end.ssh -vv– will inform you low level on both ends.ssh -vvv– will inform you about everything from both ends.
The following command will run SSH in the first level of verbosity, which gives us lots of debugging information as shown.
[email protected] ~ $ ssh -v [email protected]
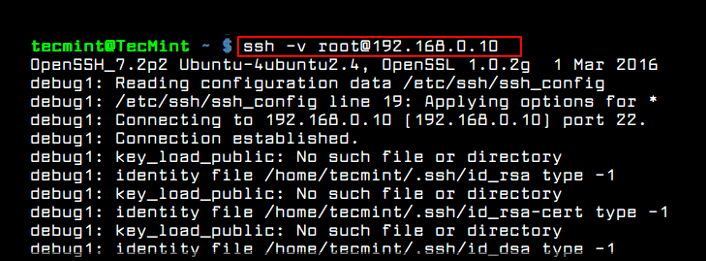
Sample Output
OpenSSH_7.2p2 Ubuntu-4ubuntu2.2, OpenSSL 1.0.2g-fips 1 Mar 2016 debug1: Reading configuration data /home/aaronkilik/.ssh/config debug1: /home/aaronkilik/.ssh/config line 18: Applying options for * debug1: Reading configuration data /etc/ssh/ssh_config debug1: /etc/ssh/ssh_config line 19: Applying options for * debug1: Connecting to 192.168.56.10 [192.168.56.10] port 22. debug1: Connection established. debug1: identity file /home/aaronkilik/.ssh/id_rsa type 1 debug1: key_load_public: No such file or directory debug1: identity file /home/aaronkilik/.ssh/id_rsa-cert type -1 debug1: key_load_public: No such file or directory debug1: identity file /home/aaronkilik/.ssh/id_dsa type -1 debug1: key_load_public: No such file or directory debug1: identity file /home/aaronkilik/.ssh/id_dsa-cert type -1 debug1: key_load_public: No such file or directory debug1: identity file /home/aaronkilik/.ssh/id_ecdsa type -1 debug1: key_load_public: No such file or directory debug1: identity file /home/aaronkilik/.ssh/id_ecdsa-cert type -1 debug1: key_load_public: No such file or directory debug1: identity file /home/aaronkilik/.ssh/id_ed25519 type -1 debug1: key_load_public: No such file or directory debug1: identity file /home/aaronkilik/.ssh/id_ed25519-cert type -1 debug1: Enabling compatibility mode for protocol 2.0 debug1: Local version string SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.2 debug1: Remote protocol version 2.0, remote software version OpenSSH_7.4 debug1: match: OpenSSH_7.4 pat OpenSSH* compat 0x04000000 debug1: Authenticating to 192.168.56.10:22 as 'tecmint' debug1: SSH2_MSG_KEXINIT sent debug1: SSH2_MSG_KEXINIT received debug1: kex: algorithm: [email protected] debug1: kex: host key algorithm: ecdsa-sha2-nistp256 debug1: kex: server->client cipher: [email protected] MAC: compression: [email protected] debug1: kex: client->server cipher: [email protected] MAC: compression: [email protected] debug1: expecting SSH2_MSG_KEX_ECDH_REPLY debug1: Server host key: ecdsa-sha2-nistp256 SHA256:1778erqyug4tHJa7D6y/Ep4UWsUtNEOBSMaj32k9oO8 debug1: Host '192.168.56.10' is known and matches the ECDSA host key. debug1: Found key in /home/aaronkilik/.ssh/known_hosts:8 debug1: rekey after 134217728 blocks debug1: SSH2_MSG_NEWKEYS sent debug1: expecting SSH2_MSG_NEWKEYS debug1: rekey after 134217728 blocks debug1: SSH2_MSG_NEWKEYS received debug1: SSH2_MSG_EXT_INFO received debug1: kex_input_ext_info: server-sig-algs=<rsa-sha2-256,rsa-sha2-512> debug1: SSH2_MSG_SERVICE_ACCEPT received debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic,password debug1: Next authentication method: publickey debug1: Offering RSA public key: /home/aaronkilik/.ssh/id_rsa debug1: Server accepts key: pkalg rsa-sha2-512 blen 279 debug1: Enabling compression at level 6. debug1: Authentication succeeded (publickey). Authenticated to 192.168.56.10 ([192.168.56.10]:22). debug1: channel 0: new [client-session] debug1: Requesting [email protected] debug1: Entering interactive session. debug1: pledge: network debug1: client_input_global_request: rtype [email protected] want_reply 0 debug1: Sending environment. debug1: Sending env LC_PAPER = lg_UG.UTF-8 debug1: Sending env LC_ADDRESS = lg_UG.UTF-8 debug1: Sending env LC_MONETARY = lg_UG.UTF-8 debug1: Sending env LC_NUMERIC = lg_UG.UTF-8 debug1: Sending env LC_TELEPHONE = lg_UG.UTF-8 debug1: Sending env LC_IDENTIFICATION = lg_UG.UTF-8 debug1: Sending env LANG = en_US.UTF-8 debug1: Sending env LC_MEASUREMENT = lg_UG.UTF-8 debug1: Sending env LC_NAME = lg_UG.UTF-8 Last login: Sat Jan 6 16:20:11 2018 from 192.168.56.1
When trying to log out or exit the session, you will also see debugging messages as shown.
[[email protected] ~]$ exit logout debug1: client_input_channel_req: channel 0 rtype exit-status reply 0 debug1: client_input_channel_req: channel 0 rtype [email protected] reply 0 debug1: channel 0: free: client-session, nchannels 1 Connection to 192.168.56.10 closed. Transferred: sent 3392, received 3120 bytes, in 118.1 seconds Bytes per second: sent 28.7, received 26.4 debug1: Exit status 0 debug1: compress outgoing: raw data 1159, compressed 573, factor 0.49 debug1: compress incoming: raw data 573, compressed 1159, factor 2.02
Next, you can enable additional (level 2 and 3) verbosity for even more debugging messages as shown.
$ ssh -vv [email protected] $ ssh -vvv [email protected]
That’s It! For more usage of SSH, read the following related articles.
- How to Secure and Harden OpenSSH Server
- 5 Best Practices to Prevent SSH Brute-Force Login Attacks in Linux
- How to Find All Failed SSH login Attempts in Linux
- How to Disable SSH Root Login in Linux
- How to Setup SSH Passwordless Login in Linux
- How to Disconnect Inactive or Idle SSH Connections in Linux
We hope you find this article helpful. You can ask any questions or share thoughts via the comment form below.