Implementing DevOps is a key element for any team that is working and maintaining a large project(s). As discussed in previous subtopics, DevOps provides teams with tools and processes required to streamline workflows and provide the agility required to work efficiently, resulting in increased productivity. Thus, If your business is to remain relevant in a
Linux Certifications - DesignLinux
LFCA: Learn the Basic Concepts of Using Containers – Part 22
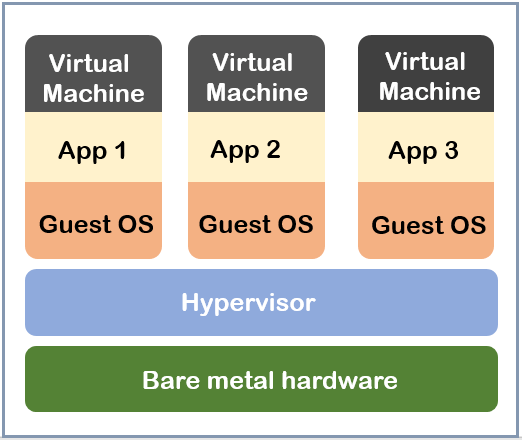
Over time, as demand for rapid testing and deployment of applications grew coupled with faster business cycles, organizations were compelled to innovate in order to keep up with the fast-paced business environment. The quest to modernize applications and build new ones to create agile workflows led to the concept of using containers. Containerization technology is
LFCA: Learn the Basic Concepts of DevOps – Part 21
DevOps has been a trending topic for quite a while now and has managed to draw the attention of technology professionals and enterprises alike. As a beginner, it can be challenging wrapping your head around the concept of DevOps, and in this topic, we will flesh out the basic concepts of this internet buzzword. To
LFCA: How to Improve Linux System Security – Part 20
As we all know, the root user is king and wields unlimited privileges over the Linux system. However non-root users are limited to basic tasks. In addition, sudo users are only granted a certain degree of root privileges as deemed fit by the root user to perform specific elevated tasks. Issues arise when regular users
LFCA: How to Improve Linux Network Security – Part 19
In an ever-connected world, network security is increasingly becoming one of the areas where organizations invest a great deal of time and resources. This is because a company’s network is the backbone of any IT infrastructure and connects all the servers and network devices. If the network is breached, the organization will pretty much be
LFCA: How to Improve Linux Network Security – Part 19
In an ever-connected world, network security is increasingly becoming one of the areas where organizations invest a great deal of time and resources. This is because a company’s network is the backbone of any IT infrastructure and connects all the servers and network devices. If the network is breached, the organization will pretty much be
LFCA – Useful Tips for Securing Data and Linux – Part 18
Since its release in the early nineties, Linux has won the admiration of the technology community thanks to its stability, versatility, customizability, and a large community of open-source developers who work round-the-clock to provide bug fixes and improvements to the operating system. By and large, Linux is the operating system of choice for public cloud,
LFCA: Basic Security Tips to Protect Linux System – Part 17
Now more than ever, we are living in a world where organizations are constantly bombarded by security breaches motivated by the acquisition of highly sensitive and confidential data which is highly valuable and makes for a huge financial reward. It’s rather surprising that despite being at a high risk of suffering from a potentially devastating
LFCA: Learn Cloud Costs and Budgeting – Part 16
Over the years, there has been an exponential adoption of Cloud services as organizations seek to tap into the numerous benefits offered by the Cloud to streamline their businesses. Most businesses have either integrated their on-premise infrastructure with the Cloud or shifted their core services to the cloud altogether. Although the Cloud provides a pay-as-you-go
LFCA: Learn Serverless Computing, Benefits and Pitfalls – Part 15
Serverless technology has generated a lot of hype in the tech community evoking a lot of curiosity and receiving some backlash to a little extent. It’s a technology that began with the launch of AWS Lamba in 2014, which was soon followed by Azure Functions later in 2016. Google later followed suit with the release