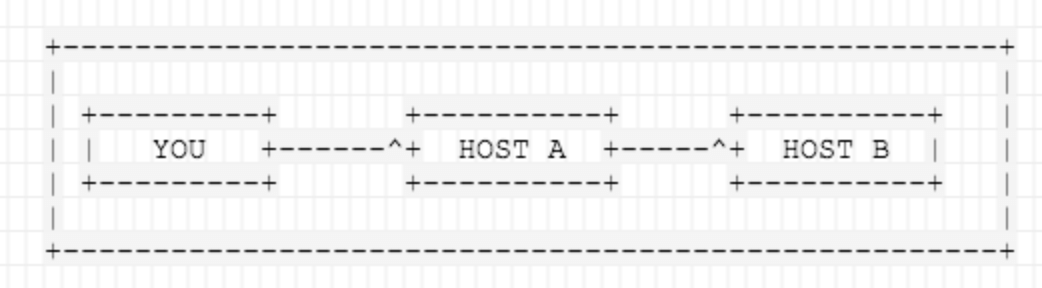
A jump host (also known as a jump server) is an intermediary host or an SSH gateway to a remote network, through which a connection can be made to another host in a different security zone, for example, a demilitarized zone (DMZ). It bridges two dissimilar security zones and offers controlled access between them. A
Security - DesignLinux
How to Secure Apache with Let’s Encrypt SSL Certificate on CentOS 8
Securing your web server is always one of the key factors that you should consider before going live with your website. A security certificate is critical for securing traffic sent from web browsers to web servers and in so doing, it’ll inspire users to exchange data with your website in the full knowledge that the
How to Use Port Knocking To Secure SSH Service in Linux
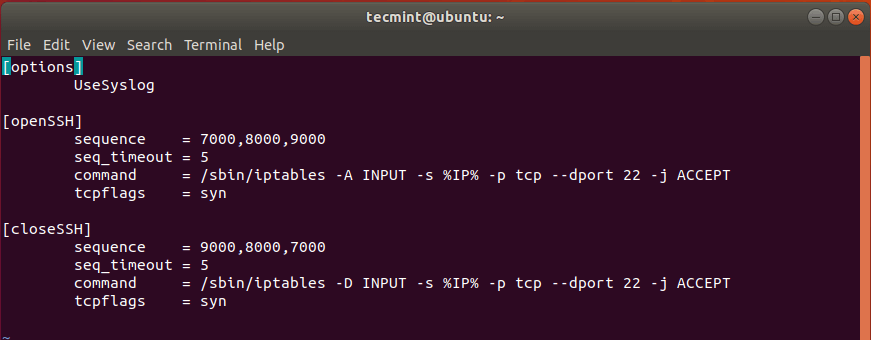
Port Knocking is a nifty technique of controlling access to a port by only allowing legitimate users access to the service running on a server. It works in such a way that when the right sequence of connection attempts is made, the firewall gladly opens the port that was closed. The logic behind port knocking
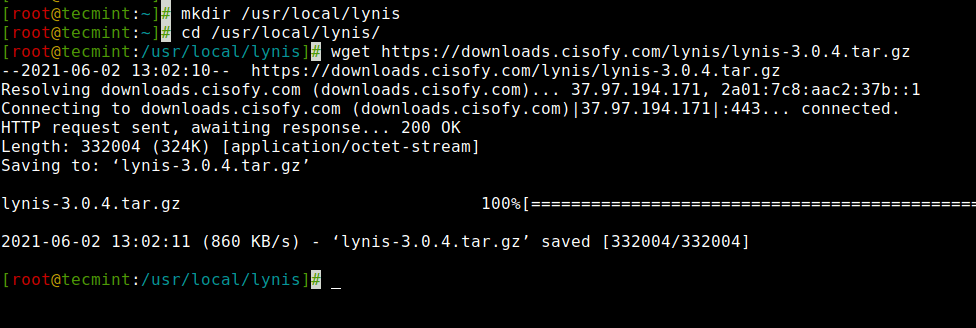
How to Do Security Auditing of Linux System Using Lynis Tool
Lynis is an open-source and much powerful auditing tool for Unix/Linux-like operating systems. It scans the system for security information, general system information, installed and available software information, configuration mistakes, security issues, user accounts without a password, wrong file permissions, firewall auditing, etc. Lynis is one of the most trusted automated auditing tools for software
LFCA: How to Improve Linux System Security – Part 20
As we all know, the root user is king and wields unlimited privileges over the Linux system. However non-root users are limited to basic tasks. In addition, sudo users are only granted a certain degree of root privileges as deemed fit by the root user to perform specific elevated tasks. Issues arise when regular users
LFCA: How to Improve Linux Network Security – Part 19
In an ever-connected world, network security is increasingly becoming one of the areas where organizations invest a great deal of time and resources. This is because a company’s network is the backbone of any IT infrastructure and connects all the servers and network devices. If the network is breached, the organization will pretty much be
LFCA: How to Improve Linux Network Security – Part 19
In an ever-connected world, network security is increasingly becoming one of the areas where organizations invest a great deal of time and resources. This is because a company’s network is the backbone of any IT infrastructure and connects all the servers and network devices. If the network is breached, the organization will pretty much be
LFCA – Useful Tips for Securing Data and Linux – Part 18
Since its release in the early nineties, Linux has won the admiration of the technology community thanks to its stability, versatility, customizability, and a large community of open-source developers who work round-the-clock to provide bug fixes and improvements to the operating system. By and large, Linux is the operating system of choice for public cloud,
LFCA: Basic Security Tips to Protect Linux System – Part 17
Now more than ever, we are living in a world where organizations are constantly bombarded by security breaches motivated by the acquisition of highly sensitive and confidential data which is highly valuable and makes for a huge financial reward. It’s rather surprising that despite being at a high risk of suffering from a potentially devastating
How to Configure FirewallD in RHEL, CentOS and Fedora
Net-filter as we all know it’s a firewall in Linux. Firewalld is a dynamic daemon to manage firewalls with support for network zones. In the earlier version, RHEL & CentOS 6 we have been using iptables as a daemon for packet filtering framework. In RHEL/CentOS 7/8 and Fedora iptables interface is being replaced by firewalld.