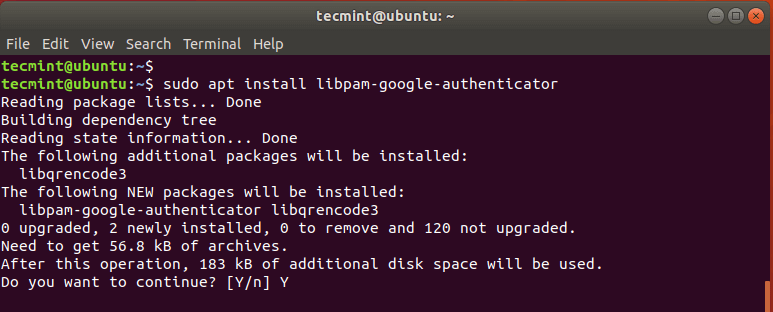
Over time, the traditional username and password authentication has proven inadequate in providing robust security to applications and systems. Usernames and passwords can easily be cracked using a plethora of hacking tools, leaving your system vulnerable to breaches. For this reason, any company or entity that takes security seriously needs to implement 2-Factor authentication. Colloquially
Security - Page 2 of 2 - DesignLinux
Setup Passwordless SSH Login for Multiple Remote Servers Using Script
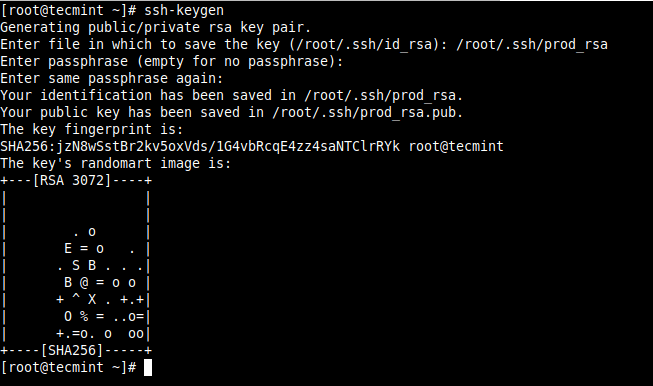
SSH Key-based authentication (also known as public-key authentication) allows for password-less authentication and it is a more secure and a much better solution than password authentication. One major advantage of SSH password-less login, let alone security is that it allows for automation of various kinds of cross-server processes. Related Read: How to Secure and Harden
How to Open Port for a Specific IP Address in Firewalld
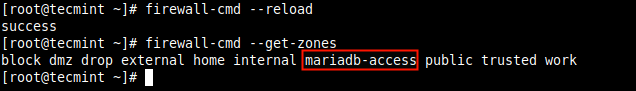
How can I allow traffic from a specific IP address in my private network or allow traffic from a specific private network through firewalld, to a specific port or service on a Red Hat Enterprise Linux (RHEL) or CentOS server? In this short article, you will learn how to open a port for a specific
Tor Browser: An Ultimate Web Browser for Anonymous Web Browsing in Linux
The primary Application we require to perform our internet activity is a browser, a web browser to be more perfect. Over the Internet, most of our’s activity is logged to the Server/Client machine which includes IP address, Geographical Location, search/activity trends and a whole lot of information which can potentially be very harmful if used
How to Create a Local Self-Signed SSL Certificate on CentOS 8
SSL (Secure Socket Layer), and its improved version, TLS (Transport Socket Layer), are security protocols that are used to secure web traffic sent from a client’s web browser to a web server. An SSL certificate is a digital certificate that creates a secure channel between a client’s browser and a web server. In so doing,