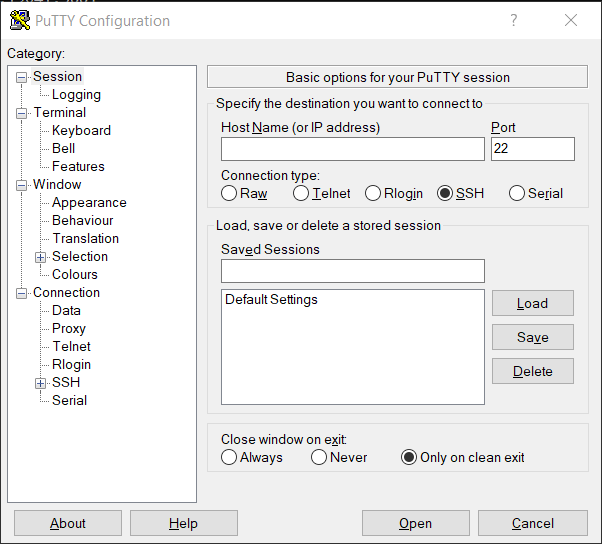
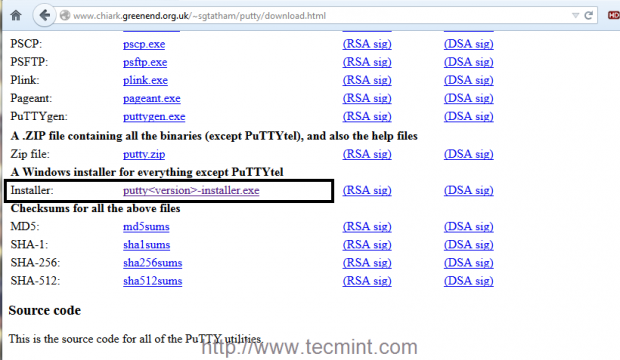
Putty is an open-source terminal emulator that supports several network protocols like Telnet, SSH, Rlogin, SCP, and Raw Socket. The initial version of putty is dated back to January 8, 1999, and was designed for the Windows Operating system but now it is supporting other operating systems like macOS and Linux too. But I have
SSH - DesignLinux
How to Access a Remote Server Using a SSH Jump Host
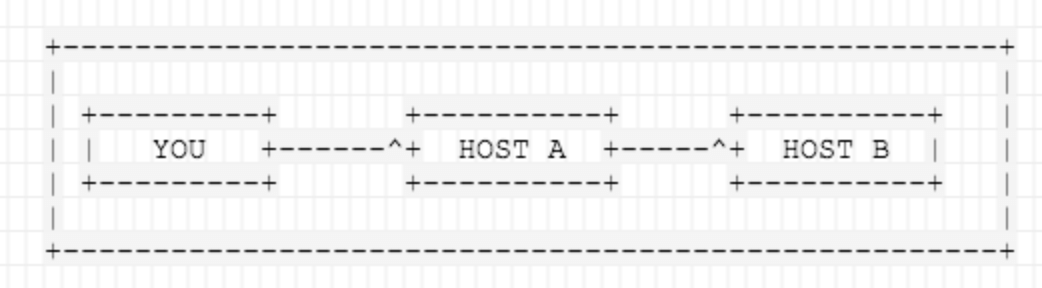
A jump host (also known as a jump server) is an intermediary host or an SSH gateway to a remote network, through which a connection can be made to another host in a different security zone, for example, a demilitarized zone (DMZ). It bridges two dissimilar security zones and offers controlled access between them. A
Enable Debugging Mode in SSH to Troubleshoot Connectivity Issues
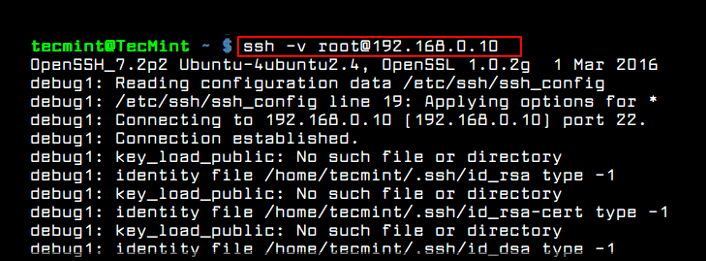
In this article, we will show you how to turn on debugging mode while running SSH in Linux. This will enable you to see what actually unfolds when you execute an ssh command to connect to a remote Linux server using the verbose mode or debugging mode. [ You might also like: 4 Ways to
Configure “No Password SSH Keys Authentication” with PuTTY on Linux Servers
SSH (Secure SHELL) is one of the most used network protocols to connect and login to remote Linux servers, due to its increased security provided by its cryptographic secure channel established for data flow over insecure networks and its Public Key Authentication. While using SSH passwords to log in to remote Linux servers can provide
How to Setup SSH Passwordless Login in Linux [3 Easy Steps]
SSH (Secure SHELL) is an open-source and most trusted network protocol that is used to log in to remote servers for the execution of commands and programs. It is also used to transfer files from one computer to another computer over the network using a secure copy (SCP) command and Rsync command. [ You might
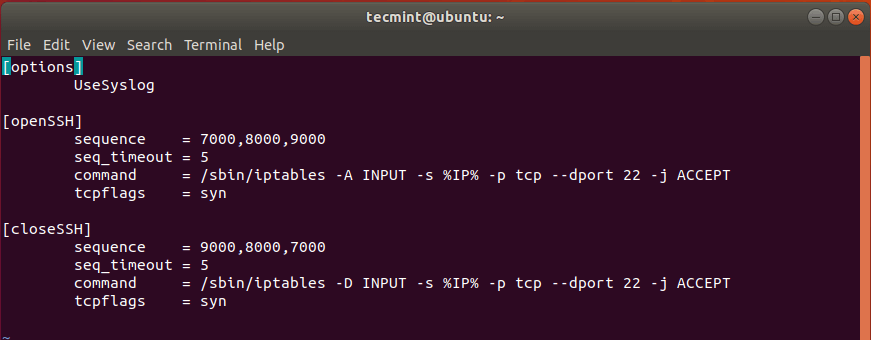
How to Use Port Knocking To Secure SSH Service in Linux
Port Knocking is a nifty technique of controlling access to a port by only allowing legitimate users access to the service running on a server. It works in such a way that when the right sequence of connection attempts is made, the firewall gladly opens the port that was closed. The logic behind port knocking
How to Install Mosh Shell as SSH Alternative on Linux
Mosh, which stands for Mobile Shell is a command-line application which is used for connecting to the server from a client computer, over the Internet. It can be used as SSH and contains more feature than Secure Shell. It is an application similar to SSH, but with additional features. The application is written originally by
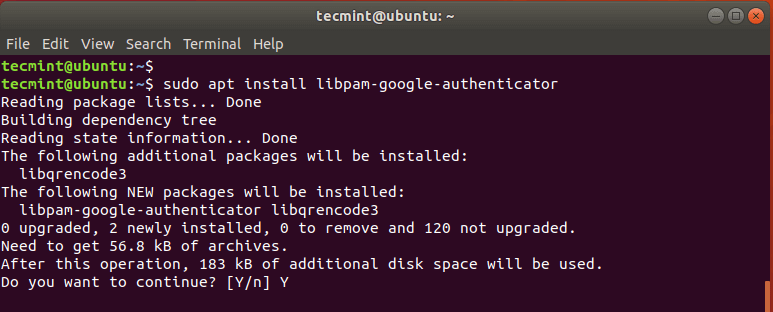
How to Use Two-Factor Authentication with Ubuntu
Over time, the traditional username and password authentication has proven inadequate in providing robust security to applications and systems. Usernames and passwords can easily be cracked using a plethora of hacking tools, leaving your system vulnerable to breaches. For this reason, any company or entity that takes security seriously needs to implement 2-Factor authentication. Colloquially
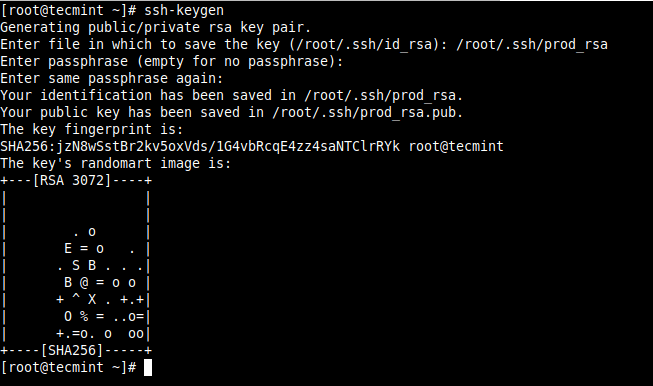
Setup Passwordless SSH Login for Multiple Remote Servers Using Script
SSH Key-based authentication (also known as public-key authentication) allows for password-less authentication and it is a more secure and a much better solution than password authentication. One major advantage of SSH password-less login, let alone security is that it allows for automation of various kinds of cross-server processes. Related Read: How to Secure and Harden