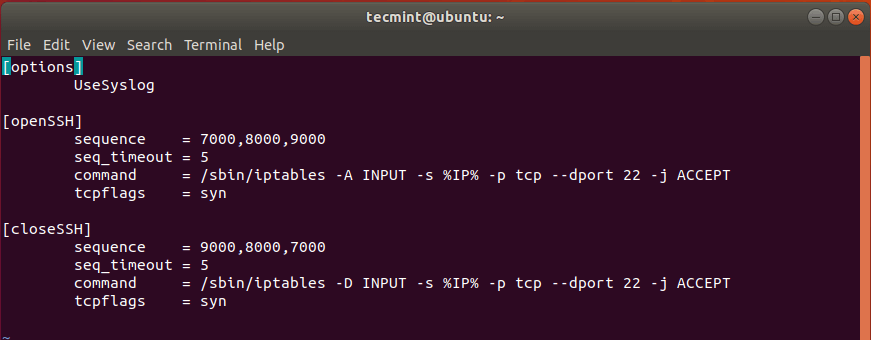
Port Knocking is a nifty technique of controlling access to a port by only allowing legitimate users access to the service running on a server. It works in such a way that when the right sequence of connection attempts is made, the firewall gladly opens the port that was closed. The logic behind port knocking
Linux Security Tips - DesignLinux
LFCA: How to Improve Linux Network Security – Part 19
In an ever-connected world, network security is increasingly becoming one of the areas where organizations invest a great deal of time and resources. This is because a company’s network is the backbone of any IT infrastructure and connects all the servers and network devices. If the network is breached, the organization will pretty much be
LFCA: How to Improve Linux Network Security – Part 19
In an ever-connected world, network security is increasingly becoming one of the areas where organizations invest a great deal of time and resources. This is because a company’s network is the backbone of any IT infrastructure and connects all the servers and network devices. If the network is breached, the organization will pretty much be
LFCA: Basic Security Tips to Protect Linux System – Part 17
Now more than ever, we are living in a world where organizations are constantly bombarded by security breaches motivated by the acquisition of highly sensitive and confidential data which is highly valuable and makes for a huge financial reward. It’s rather surprising that despite being at a high risk of suffering from a potentially devastating
Setup Passwordless SSH Login for Multiple Remote Servers Using Script
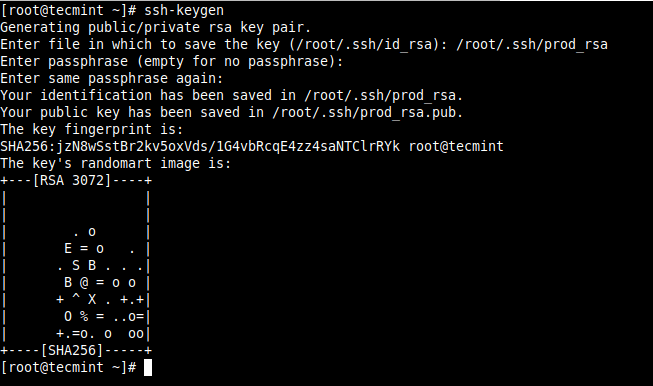
SSH Key-based authentication (also known as public-key authentication) allows for password-less authentication and it is a more secure and a much better solution than password authentication. One major advantage of SSH password-less login, let alone security is that it allows for automation of various kinds of cross-server processes. Related Read: How to Secure and Harden